An Internal Pen Test Simulates Which of the Following
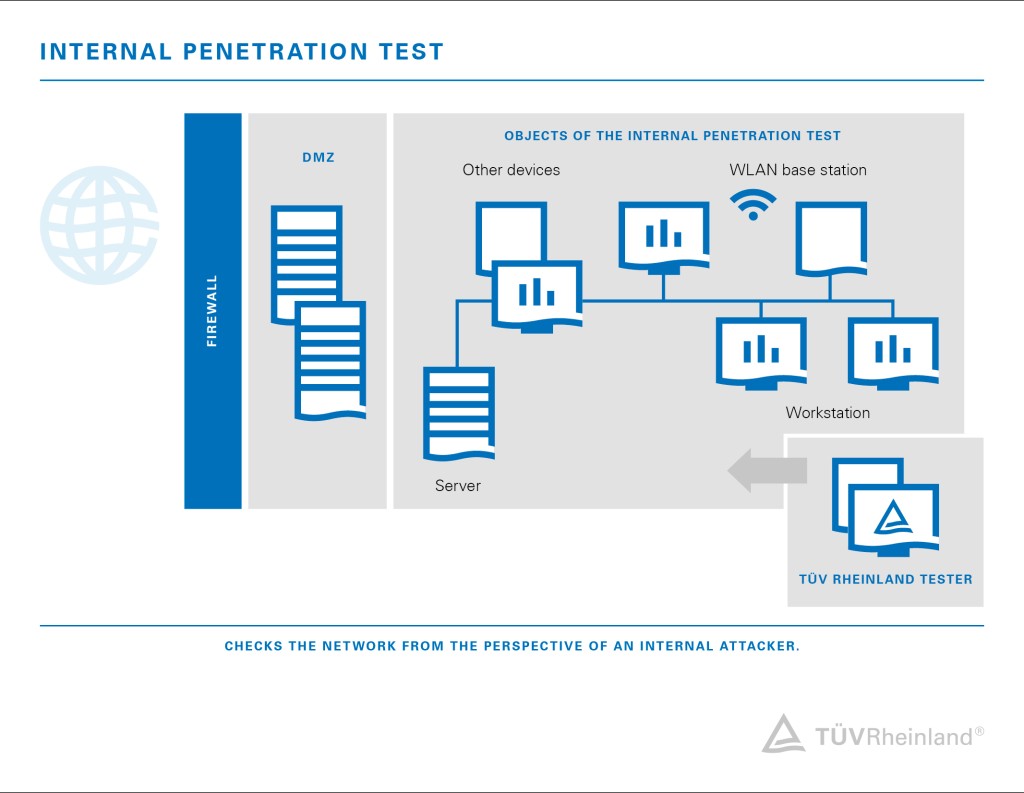
A pen test is a form of ethical cyber security assessment conducted to identify safely exploit and help eliminate vulnerabilities that reside across an organisations on-premises and remote IT environments. Commonly referred to as an Internal Pen Test the internal infrastructure penetration test focuses on testing attacks which could be carried out by an adversary who has already gained a foothold within your network and is looking to elevate themselves to gain further control and cause more damage.

Types Of Penetration Test What S The Difference Comtact
Our network penetration test follows an internationally recognized comprehensive methodology particularly the Penetration Testing Execution Standard PTES.
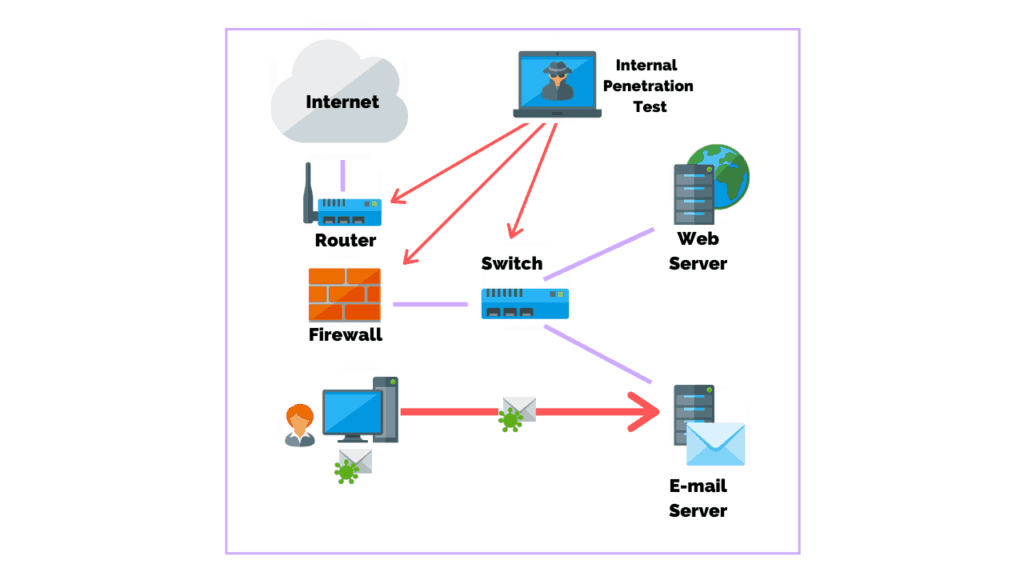
. The first method is internal testing which simulates the damage that employees could unknowingly make on your systems. While internal penetration testing is performed less frequently it is also a great asset for risk management strategies. Internal network penetration test.
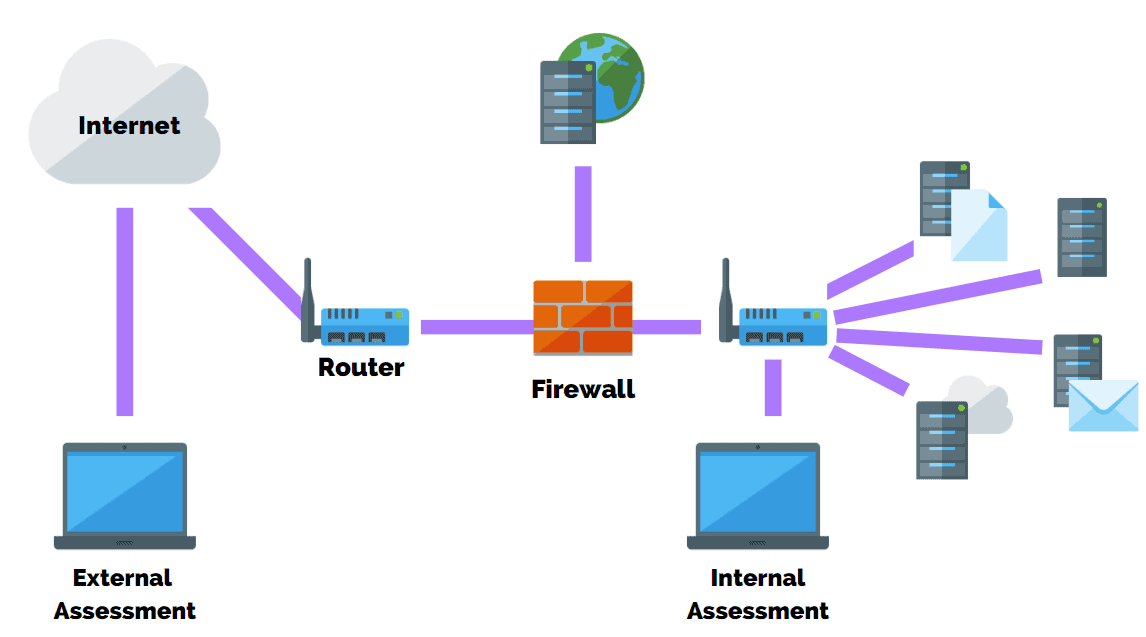
Internal testing simulates what an insider attack could accomplish while an external test exploits vulnerabilities to identify information that will be exposed to the outside world. Pen tests can be automated with software applications or they can be performed manually. An internal penetration test by contrast simulates either the actions a hacker might take once access has been gained to a network or those of a malicious actor or disgruntled employee with access that he or.
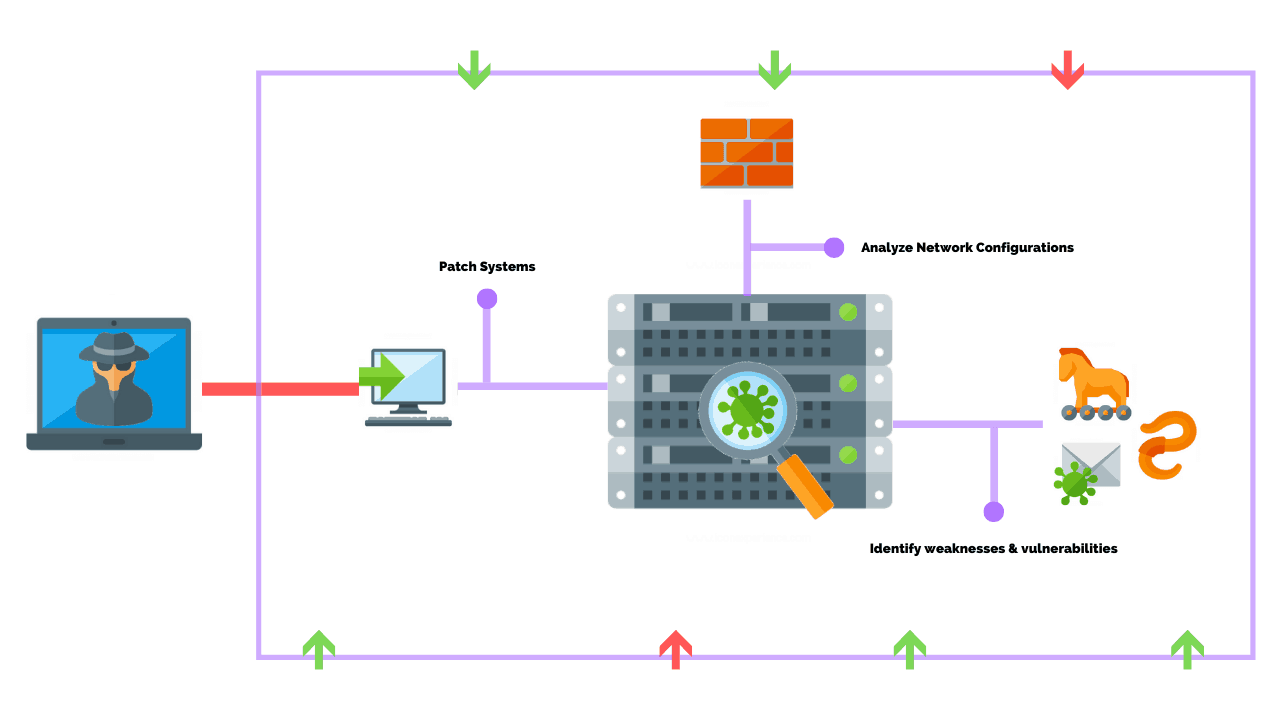
During an assessment your pen test team discovers child porn on a system. This type of penetration testing assumes that a malicious party somehow has access to your network. The following are four ways of performing a pen test.
Penetration testing also called pen testing is the practice of testing a computer system network or Web application to find vulnerabilities that an attacker could exploit. A Red Team project closely simulates a real-world hack with Interteks experts assessing potential organizational weaknesses gathering intelligence and then launching a mock cyber-attack in real time using similar techniques to real hackers such as phishing attacks. White box testing c.
Which of the following is the appropriate response. This test simulates an attempt to access the organizations critical business assets by an unauthorized or unwanted party. Why Internal Penetration Testing Is Important.
During a penetration test specifically scoped to a single web application Chris discovers that the web server also contains a list of passwords to other servers at the target location. Enterokinase stimulates which of the following. IPV Security offers a range of pen-tests both at the infrastructure level and at the application level.
A penetration test commonly known as a pentest is a security assessment which simulates the malicious activities of real-world attackers to identify security holes in your businesss systems or applications. Either way the process includes gathering information about the target before the test. It could be a disgruntled employee or a skilled hacker using a variety of techniques to break in.
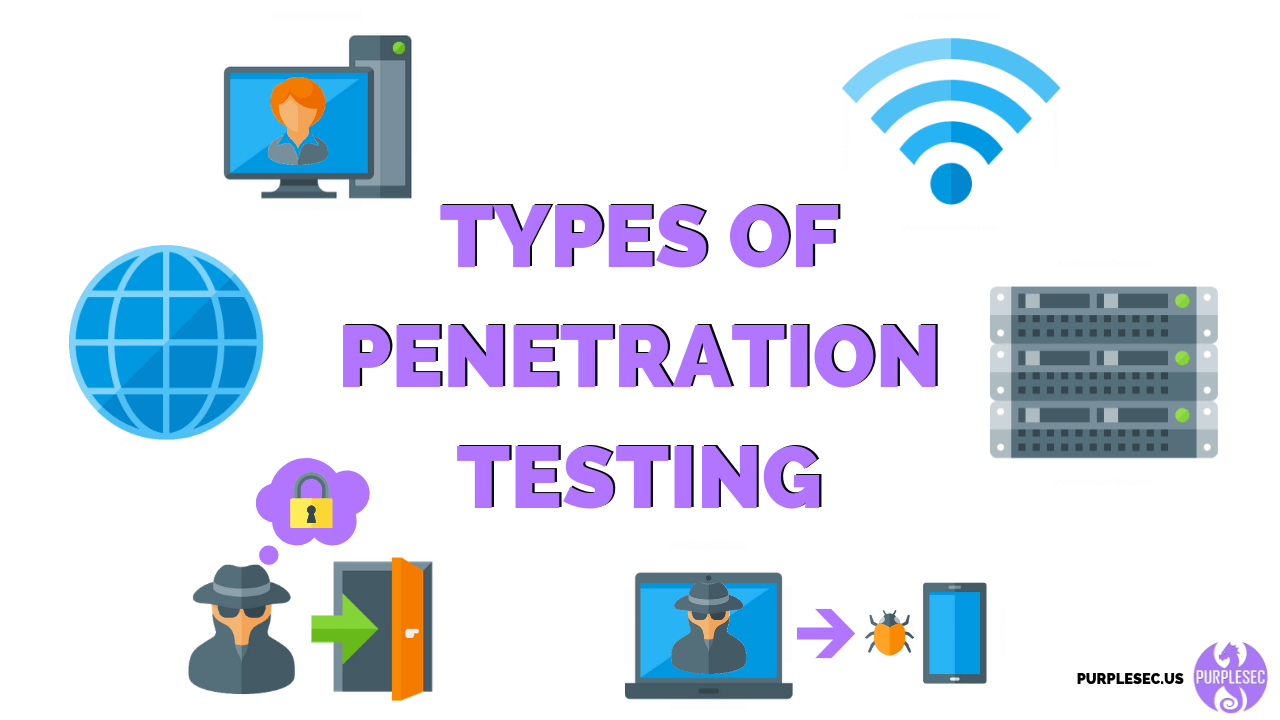
Ways to Perform Pen Tests. There are generally four different ways of performing a penetration test. Scanning and Network Mapping.
A penetration test also known as a pen test is a simulated cyber attack against your computer system to check for exploitable vulnerabilities. The second method is external testing which simulates the damage outside attacks could make on your visible DNS web servers email servers and firewalls. You need to conduct a penetration test for a client that best assesses the target organizations vulnerability to a malicious insider who has the network privileges of an average employee.
Penetration testing also called pen testing is the practice of testing a computer system network or Web application to find vulnerabilities that an attacker could exploit. As well as traditional pen testing Intertek also provides Red Teaming services. After he notifies the client they ask him to use them to validate those servers and he proceeds to test those passwords against the other servers.
It is also used to determine the potential spread of a malware such as. Cease testing immediately and refuse to continue work for the client. Correct option is.
Which type of penetration test best simulates an outsider attack. Penetration testing or Pen testing simulates an actual attack on the network Pen from CSIS 2320 at Salt Lake Community College. One of the most basic tools in assessing the data security state is a penetration test.
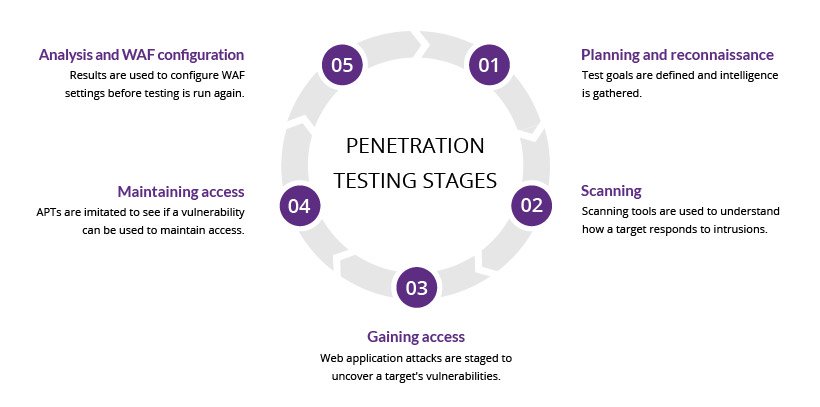
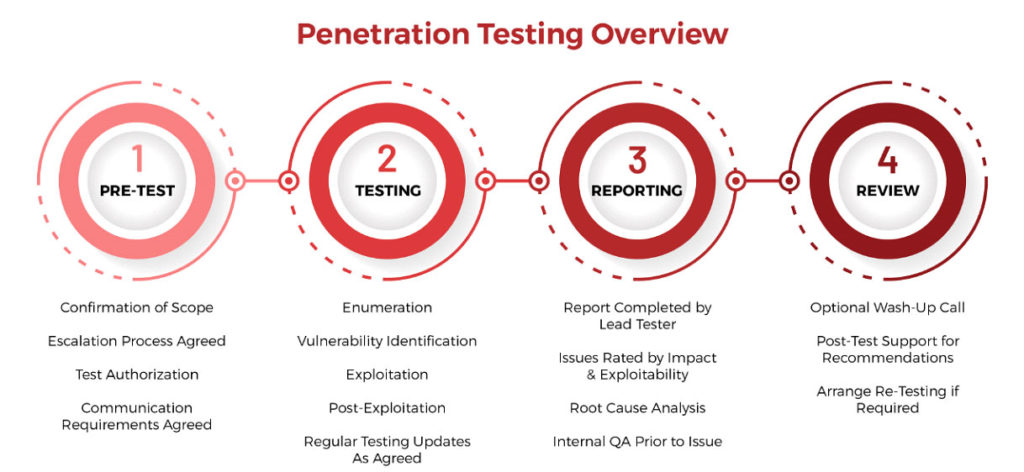
The test simulates a malicious insider. It also deals with security holes that could be taken. In short our test is composed of the following stages.
Which of the following is a test wherein the pen-tester has partial knowledge about the target systemnetwork. It allows organizations to assess their internal networks and to uncover vulnerabilities that could be exploited internally by malicious employees or business partners. Continue testing but report findings to the business owners.
Pen tests can be automated with software applications or they can be performed manually. Continue testing and report findings at out-brief. Black box testing b.
Internal penetration testing simulates an attack on your organization that originates from within it. In the context of web application security penetration testing is commonly used to augment a web application firewall WAF. One of the great things about an IPT is that if done properly it holistically tests vulnerabilities passwords network config and internal monitoring controls.
Pen testing can involve the attempted breaching of any number of application. Which type of penetration test requires the most time and. Enterokinase also called enteropeptidase is a proteolytic enzyme secreted from the duodenal mucosa that changes the inactive pancreatic secretion trypsinogen into trypsin one of the.
Which of the following is one of the important documents to be signed before the penetration test to safeguard interest of the concerned parties. It is recommended that all organisations commission security testing at least once per year with additional assessments following significant changes to. These tests can be performed with no prior knowledge Black-Box or with.
Because only the most. Which type of test should you perform. Gray box testing d.
Either way the process includes gathering information about the target before the test. PCI pen test to assess the technical and operational components of your system to ensure cardholder and payment data security systems meet the set PCI compliance standards. This test simulates an attack from within the network if a malicious actor were to gain a foothold on an internal asset which can be what happens when an employee opens that attachment they werent supposed to.
The aim of conducting a pen test is to understand what vulnerabilities are in your business systems how they could be exploited and what the. Simulates the damage that employees could wreak on your systems.

The Difference Between A Penetration Test And Vulnerability Assessment 2 Of 2 Secure Ops

What Are The Steps To Conducting An Internal Pen Test Rsi Security
What Are The Different Types Of Penetration Testing Purplesec

What Is Penetration Testing Definition Stages Techniques Pros And Cons

External Vs Internal Penetration Test What S The Difference
Professional Pen Testing Company Penetration Testing Service
How To Perform A Successful Network Penetration Test Purplesec
Penetration Testing Information Security Buzz
The Difference Between A Penetration Test And Vulnerability Assessment 2 Of 2 Secure Ops

What You Need To Know About Internal Penetration Tests Pci Dss Guide

Internal Penetration Testing Network Pen Test

What Is An Internal Penetration Test And How Is It Done Reciprocity

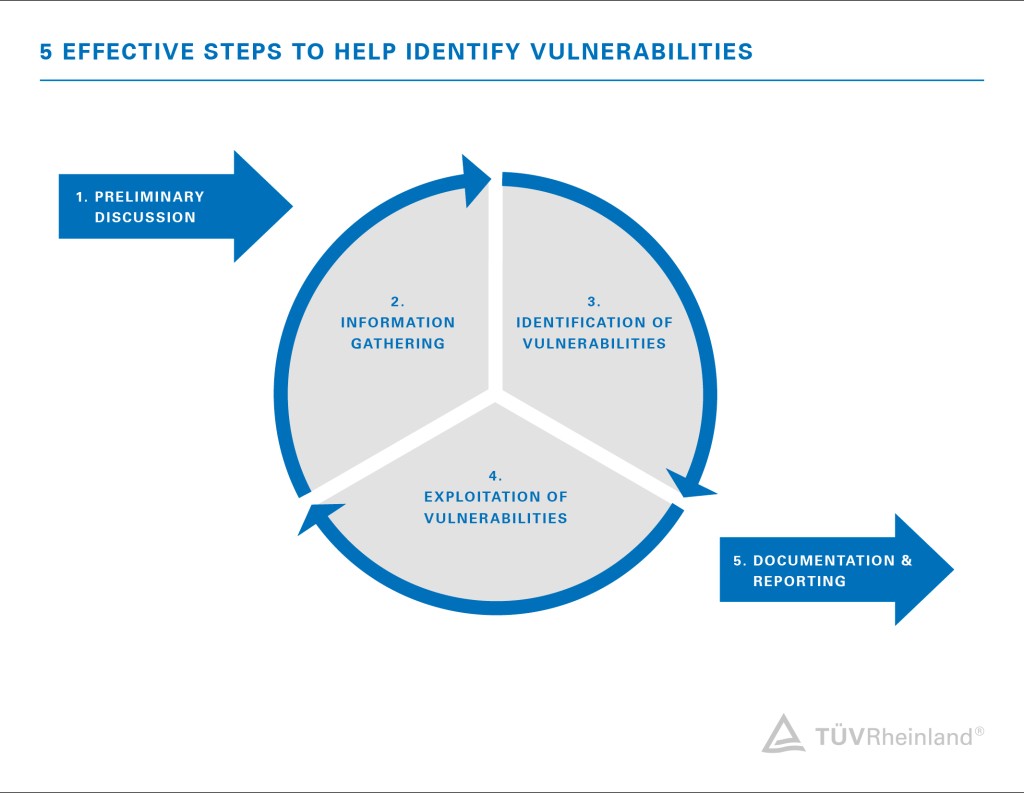
Penetration Test Jo Tuv Rheinland
What Are The Different Types Of Penetration Testing Purplesec
Penetration Test Jo Tuv Rheinland

Pen Testing Guide Types Steps Methodologies And Frameworks

.jpg?width=726&name=Pen%20Test%20Cycle%20graphic%20(clean).jpg)
Comments
Post a Comment